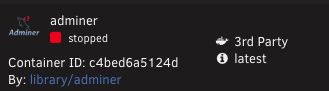
After UNRAID upgrade to 7.0.1, most docker containers now show 3rdParty and the edit option is no longer available.
** ALL DOCKER CONTAINERS ** were updated before upgrading to UNRAID 7.0.1.
Google search found the following:
https://forums.unraid.net/topic/178736-docker-container-now-shows-3rd-party
<strong><em>Trying to validate what causes the '3rdParty' indicator.</em></strong> <strong>1. make a copy </strong> cp my-ActualServer.xml my-ActualServer.xml-test <strong>2. List the files and dates</strong> ls -la *ActualServer* -rw------- 1 root root 3100 Feb 10 2025 my-ActualServer.xml -rw------- 1 root root 3100 Aug 17 19:11 my-ActualServer.xml-test -rw------- 1 root root 3120 Feb 10 2025 my-ActualServer.xml.bak <strong>3. Try the updata_container method:</strong> /usr/bin/php -q /usr/local/emhttp/plugins/dynamix.docker.manager/scripts/update_container ActualServer <strong>4. ** Files did not change **</strong> root@boomer-unraid:/boot/config/plugins/dockerMan/templates-user# ls -la *ActualServer* -rw------- 1 root root 3100 Feb 10 2025 my-ActualServer.xml -rw------- 1 root root 3100 Aug 17 19:11 my-ActualServer.xml-test -rw------- 1 root root 3120 Feb 10 2025 my-ActualServer.xml.bak<strong><em>I noticed that the container ID has changed:</em></strong> WAS: Container ID: e320a955b34e NOW: Container ID: a52e79d53c2e <strong>Looking into container....</strong> docker inspect ActualServer "Labels": { "net.unraid.docker.icon": "https://github.com/actualbudget/actual/raw/master/packages/desktop-electron/icons/icon.png", "net.unraid.docker.managed": "dockerman", "net.unraid.docker.webui": "http://[IP]:[PORT:5006]" } <strong>Interesting....</strong>
Let’s look at another example:
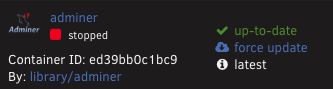
<strong>1. Dump container before update and verify no labels exists</strong> docker inspect adminer > 00-adminer.yaml <strong>2. Update container</strong> /usr/bin/php -q /usr/local/emhttp/plugins/dynamix.docker.manager/scripts/update_container adminer <strong>3. Dump container after the update and verify labels exist</strong> docker inspect adminer > 01-adminer.yaml <strong>4. Compare the two files</strong> sdiff 00-adminer.yaml 01-adminer.yaml <strong><em>** Yep, update_container difinately added the net.unraid labels as seen below:</em></strong>
Some cool ways to identify containers with labels
Find running containers with specific label<strong>docker ps --filter "label=net.unraid.docker.managed=dockerman" --format "{{.ID}}\t{{.Names}}\t{{.Label \"net.unraid.docker.managed\"}}"</strong> 3caede5f1732 nextcloud-mysql dockerman 4e07f60e6acb MongoDB dockerman 3b7a41697423 Gitea dockerman d0d55a2ec4a0 WordPress dockerman 298b7df6aafe MQTT dockerman 532eba7ffd48 netdata dockerman 1f467bd29e8e dashy dockerman 549f472399ac opengist dockerman b7614ff4a36e Postgres12.5 dockerman ddd65aaa2e9b snipe-it dockerman a39d5f5c0e18 duckdns-tryitog dockerman
Same as above but for any container running or not<strong>docker ps -a --filter "label=net.unraid.docker.managed=dockerman" --format "{{.ID}}\t{{.Names}}\t{{.Label \"net.unraid.docker.managed\"}}"</strong> 8d7a299bff28 binhex-krusader dockerman ed39bb0c1bc9 adminer dockerman a52e79d53c2e ActualServer dockerman 480c27f54d50 IT-Tools dockerman 9535a06b9e26 linkace dockerman c54a31cccfc6 triliumnext dockerman ad42b0e030c4 NginxProxyManager dockerman 00511cf4b0d3 linkding dockerman a1ea55c0444d Zoneminder dockerman c62bd0d59d28 freecad dockerman 2358b48ed0b9 Bitfocus-Companion dockerman 5ff8840228ec kicad dockerman e0cc0c736037 Cloudflare-DDNS dockerman 3caede5f1732 nextcloud-mysql dockerman 9691261688a7 baserow dockerman 4e07f60e6acb MongoDB dockerman 56be5dd0db23 CodeChef dockerman f99aba96e044 GitLab-CE dockerman e33d9e34ad8c n8n dockerman 3b7a41697423 Gitea dockerman d0d55a2ec4a0 WordPress dockerman cc5ac7b02ca7 Wekan dockerman d17d96056424 Excalidraw dockerman a3a2beae0982 Ntfy dockerman ba79f9557101 pydio-cells dockerman 73c2d98b6cf0 Ghostfolio dockerman 49a6c5312c42 postgresql13 dockerman 23226226a1cb Wallos dockerman 6184ee2f9372 mosquitto dockerman 11f855d44c61 thingsboard-postgres dockerman 298b7df6aafe MQTT dockerman 39ac708d4ace Hugo dockerman 791e839baacf Gitea-Runner dockerman 8af1750d1918 github-backup dockerman 5ff73e22c94d Hoppscotch dockerman 98cd28c50280 netbox3x dockerman 0f56f61654d6 goStatic-Publii dockerman 532eba7ffd48 netdata dockerman 1f467bd29e8e dashy dockerman 549f472399ac opengist dockerman 48d00e1988f1 piwigo dockerman 965ef19a7499 duckdns-earnhardt.home dockerman 9b8d80044068 CaddyV2 dockerman 2a618090df2e Authelia dockerman 956ab0253c37 postgresql17 dockerman b7614ff4a36e Postgres12.5 dockerman 102917bfb04e lychee dockerman 1914ffe0bc9c keycloak dockerman c78dfd7f9c62 duplicati dockerman 3d4bc2006b51 code-server dockerman 426827d60851 activepieces dockerman 71d3bf4d4942 Jenkins dockerman b30cbc3af59d dokuwiki dockerman ddd65aaa2e9b snipe-it dockerman dcb167684157 Appsmith dockerman 761e61f75706 invoiceninja-v5 dockerman 40f89e92a5d5 netbootxyz dockerman ed3862483f6a SearXNG dockerman f5c182db66e3 raneto dockerman 1c7c8c04dbda QDirStat dockerman 8a1433c7f07d FileZilla dockerman 412d2b653f36 dupeGuru dockerman 7d7441c84d48 duckdns-earnhardt3rd dockerman a39d5f5c0e18 duckdns-tryitog dockerman 135a029d86f5 duckdns-wm.frank.earnhardt dockerman 542572ac8522 digikam dockerman dc5d459fdd88 archivebox-FE dockerman 345e970aabc1 archivebox dockerman 30aaeeb769aa Czkawka dockerman 41627ba8f3a9 Dependency-Track-FrontEnd dockerman 89f80b73219a Dependency-Track-API-Server dockerman
Show all container without UNRAID labels<strong>docker ps -a --format "{{.ID}}\t{{.Names}}\t{{.Label \"net.unraid.docker.managed\"}}"|grep -v dockerman|grep -v composeman</strong> <strong><em>** ALL OF THESE WILL NEED TO BE FIXED **</em></strong> e1637da65978 wp_web a8a7e83f597f wp_db e5f310b830dc wallabag 9573861e0d06 huginn df91a745e1ef vm_custom_icons a0b36d5cbbc5 telegraf 007ca2b46425 swag ce6553006949 solr 5654c41016e9 RustDeskServer 12a4b2a2a832 rsnapshot efc6dc95a638 rancher 86d0bbbd2b8c prometheus 1422bade0c75 pihole-template d8582dc49279 phpmyadmin 193b398ad0ee Photoview 0b399fa37bff pgadmin4 808e3505bde4 organizrv2 13df9df1739c observium 3684cb7bb3ca librenms 33810766744b Grafana 56f936f6eced gotify 4ed92f4fdea6 focalboard b67cd095fae7 evershop 94385e2980d2 ESPHome 707c9c1ec6e5 docker-wyze-bridge dc8ec04d3873 db-backup 124f818da4a0 DiskSpeed 91baee070fbd CouchDB-Offical-Docker-v1.x 1684dc2c8f02 CloudBeaver 4f684d93040a cassandra a7c6652ce7cf binhex-nzbget 96618ce4d86c Apache-NIFI 32ccccd95df6 idrac6 6ee81ad43deb mysql a9371455a18a dc-plausible_plausible_db_1 fc02e8b0c93f vaultwarden 64115d8ba1b5 Influxdb af9b8f4d23b0 dc_wp_bnote_web 84b0c0e3ba3f dc_wp_bnote_db f679530e44c8 NodeRed-Official-Docker 3a9888893276 Redis 307a5cd8316c Thunderbird 8183ce221e0d Rocket.Chat 681092fd0b16 kanboard 97898f2d0fcf dc-plausible_plausible_1 774a96bf12a2 DockerRegistry e7bd5ad7fc9f OpenProject13 b441de573a2d binhex-urbackup b7dd523f7b81 cyberchef e27074bdb0ab binhex-privoxyvpn 3264e1392e2b backuppc 410ba4dab171 trilium e06ecf3ef2d2 sqlserver2017 cf4a1c9cd228 JoplinApp 5c907f188750 Obsidian 7649507714c9 TiddlyWiki5 256d9e923e49 gracious_bouman 81b9e1523875 nostalgic_bouman cac10ec24621 sqlitebrowser 54968c8943b1 mariadb 9cf6e4da6b66 binhex-airsonic-advanced bedb9d02b209 dc-plausible_plausible_events_db_1 1d5839014f14 dc-plausible_mail_1 3e6c773823f3 Livebook 827959cfb85a server_self_hosted 127d2cfae1c4 localstack_self_hosted df7bbc1f2ed0 db_self_hosted f59e854f7b47 jupyterlab 6581d8e90807 dc-registry_registry_1 51c6d657d280 NoSQLClient 53ebe2ab1fae mongo-repli 766eca62d734 mongo-db2 4137dbd84498 mongo-db1 ad502266b959 mongo-db3 aae04ae883f7 rocketchat 9ae86914faac rockerchat-mongo 80c56aeadcc0 polemarch 62080d638eee scrutiny 49864741da0f homebridge 7e9a3f4bdddd Filerun-ofi 8fcb6547f854 Portainer 9ae263fd4598 Virt-Manager c0f5ca2899dc macinabox d10ed0f8f0dd goaccess-gitea d585094020da goaccess-nextcloud 8e09f2608e05 P3R-KeePassXC 4a70468ed4fe elasticsearch 4e614d8d2a11 HOOBS 9e88f9b35375 golinks 95624650bf8e smartthings-mqtt-bridge
So the docker labels are not stored in the templates files, but generated during the run process:
docker run -d --name='adminer' --net='bridge' --pids-limit 2048 -e TZ="America/New_York" -e HOST_OS="Unraid" -e HOST_HOSTNAME="boomer-unraid" -e HOST_CONTAINERNAME="adminer" -e 'ADMINER_DESIGN'='flat' -e 'ADMINER_PLUGINS'='' <strong>-l net.unraid.docker.managed=dockerman</strong> <strong>-l net.unraid.docker.webui='http://[IP]:[PORT:8080]'</strong> <strong>-l net.unraid.docker.icon='https://raw.githubusercontent.com/selfhosters/unRAID-CA-templates/master/templates/img/adminer.png'</strong> -p '8088:8080/tcp' 'adminer'
Let’s try another way to correct by example:
<strong>1. Find the image that the current Apache-NIFI container is based on: </strong> <em><strong>docker inspect Apache-NIFI</strong></em> [ { "Id": "<strong>96618ce4d86c0</strong>81b9efb014a3c6cbb0435e166339a4e6378cbe48dec3d875dd1", "Created": "2025-02-09T02:46:06.220763971Z", "Path": "../scripts/start.sh", "Args": [], "State": { "Status": "exited", "Running": false, "Paused": false, "Restarting": false, "OOMKilled": false, "Dead": false, "Pid": 0, "ExitCode": 1, "Error": "", "StartedAt": "2025-08-18T16:53:32.654950904Z", "FinishedAt": "2025-08-18T16:53:44.058582028Z" }, "Image": "sha256:<strong>c3c4056e70c0048b10f</strong>4866cab144f5aa9ef19bfa506ccefac48f11992601d78", <strong>2. UNRAID GUI Shows matching Container</strong>: Apache-NIFI Container ID: 96618ce4d86c <strong>3. Confirm the image still exists:</strong> <strong><em>docker images -a --filter "reference=apache/nifi"</em></strong> REPOSITORY TAG IMAGE ID CREATED SIZE apache/nifi latest c3c4056e70c0 6 months ago 1.58GB <strong>4. Let's Remove the existing container: 96618ce4d86c</strong> <strong><em>docker rm 96618ce4d86c</em></strong> 96618ce4d86c <strong>5. Verify container is gone:</strong> <strong><em>docker ps -a -f name=apache/nifi</em></strong> CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES <strong>6. Run Container using UNRAID RUN:</strong> <strong><em>/usr/local/emhttp/plugins/dynamix.docker.manager/scripts/docker run -d --name='Apache-NIFI' --net='bridge' --pids-limit 2048 -e TZ="America/New_York" -e HOST_OS="Unraid" -e HOST_HOSTNAME="boomer-unraid" -e HOST_CONTAINERNAME="Apache-NIFI" -l net.unraid.docker.managed=dockerman -l net.unraid.docker.webui='http://[IP]:[PORT:8080]/nifi/' -l net.unraid.docker.icon='https://d36jcksde1wxzq.cloudfront.net/be7833db9bddb4494d2a7c3dd659199a.png' -p '8084:8080/tcp' -v '/mnt/user/appdata/nifi':'/nifi':'rw' -v '/mnt/user/appdata/nifi/content':'/opt/nifi/nifi-current/content_repository':'rw' -v '/mnt/user/appdata/nifi/database':'/opt/nifi/nifi-current/database_repository':'rw' -v '/mnt/user/appdata/nifi/flowfile':'/opt/nifi/nifi-current/flowfile_repository':'rw' -v '/mnt/user/appdata/nifi/state':'/opt/nifi/nifi-current/state':'rw' -v '/mnt/user/appdata/nifi/logs':'/opt/nifi/nifi-current/logs':'rw' -v '/mnt/user/appdata/nifi/conf':'/opt/nifi/nifi-current/conf':'rw' 'apache/nifi' </em></strong> 60eb77bb97586ed0f8321a1e24c23b2d865244175fd932e479438bc2a5905b36 7. Inspect the New Container: <strong>docker inspect Apache-NIFI</strong> [ { "Id": "60eb77bb97586ed0f8321a1e24c23b2d865244175fd932e479438bc2a5905b36", "Created": "2025-08-18T17:19:14.141634087Z", "Path": "../scripts/start.sh", "Args": [], "State": { "Status": "exited", "Running": false, "Paused": false, "Restarting": false, "OOMKilled": false, "Dead": false, "Pid": 0, "ExitCode": 1, "Error": "", "StartedAt": "2025-08-18T17:19:21.051633766Z", "FinishedAt": "2025-08-18T17:19:31.454507056Z" }, "Image": "sha256:<strong>c3c4056e70c0048b10f</strong>4866cab144f5aa9ef19bfa506ccefac48f11992601d78", <strong>1. Find the image that the current Apache-NIFI container is based on: </strong> <strong><em>docker inspect Apache-NIFI</em></strong> [ { "Id": "96618ce4d86c081b9efb014a3c6cbb0435e166339a4e6378cbe48dec3d875dd1", "Created": "2025-02-09T02:46:06.220763971Z", "Path": "../scripts/start.sh", "Args": [], "State": { "Status": "exited", "Running": false, "Paused": false, "Restarting": false, "OOMKilled": false, "Dead": false, "Pid": 0, "ExitCode": 1, "Error": "", "StartedAt": "2025-08-18T16:53:32.654950904Z", "FinishedAt": "2025-08-18T16:53:44.058582028Z" }, "Image": "sha256:c3c4056e70c0048b10f4866cab144f5aa9ef19bfa506ccefac48f11992601d78", <strong>2. UNRAID GUI Shows matching Container: Apache-NIFI Container ID: 96618ce4d86c</strong> <strong>3. Configm the image still exists:</strong> <strong><em>docker images -a --filter "reference=apache/nifi"</em></strong> REPOSITORY TAG IMAGE ID CREATED SIZE apache/nifi latest c3c4056e70c0 6 months ago 1.58GB <strong>4. Let's Remove the existing container: 96618ce4d86c</strong> <strong><em>docker rm 96618ce4d86c</em></strong> 96618ce4d86c <strong>5. Verify container is gone:</strong> <strong><em>docker ps -a -f name=apache/nifi</em></strong> CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES <strong>6. Run Container using UNRAID RUN:</strong> /usr/local/emhttp/plugins/dynamix.docker.manager/scripts/docker run -d --name='Apache-NIFI' --net='bridge' --pids-limit 2048 -e TZ="America/New_York" -e HOST_OS="Unraid" -e HOST_HOSTNAME="boomer-unraid" -e HOST_CONTAINERNAME="Apache-NIFI" -l net.unraid.docker.managed=dockerman -l net.unraid.docker.webui='http://[IP]:[PORT:8080]/nifi/' -l net.unraid.docker.icon='https://d36jcksde1wxzq.cloudfront.net/be7833db9bddb4494d2a7c3dd659199a.png' -p '8084:8080/tcp' -v '/mnt/user/appdata/nifi':'/nifi':'rw' -v '/mnt/user/appdata/nifi/content':'/opt/nifi/nifi-current/content_repository':'rw' -v '/mnt/user/appdata/nifi/database':'/opt/nifi/nifi-current/database_repository':'rw' -v '/mnt/user/appdata/nifi/flowfile':'/opt/nifi/nifi-current/flowfile_repository':'rw' -v '/mnt/user/appdata/nifi/state':'/opt/nifi/nifi-current/state':'rw' -v '/mnt/user/appdata/nifi/logs':'/opt/nifi/nifi-current/logs':'rw' -v '/mnt/user/appdata/nifi/conf':'/opt/nifi/nifi-current/conf':'rw' 'apache/nifi' 60eb77bb97586ed0f8321a1e24c23b2d865244175fd932e479438bc2a5905b36 <strong>7. Inspect the New Container:</strong> <strong><em>docker inspect Apache-NIFI</em></strong> [ { "Id": "60eb77bb97586ed0f8321a1e24c23b2d865244175fd932e479438bc2a5905b36", "Created": "2025-08-18T17:19:14.141634087Z", "Path": "../scripts/start.sh", "Args": [], "State": { "Status": "exited", "Running": false, "Paused": false, "Restarting": false, "OOMKilled": false, "Dead": false, "Pid": 0, "ExitCode": 1, "Error": "", "StartedAt": "2025-08-18T17:19:21.051633766Z", "FinishedAt": "2025-08-18T17:19:31.454507056Z" }, "Image": "sha256:c3c4056e70c0048b10f4866cab144f5aa9ef19bfa506ccefac48f11992601d78", <strong><em>** Matching Image **</em></strong> BEFORE:<strong>c3c4056e70c0048b10f</strong> AFTER:<strong>c3c4056e70c0048b10f</strong>There is evidence that a container can be removed and started from the existing image without pulling the :latest update.