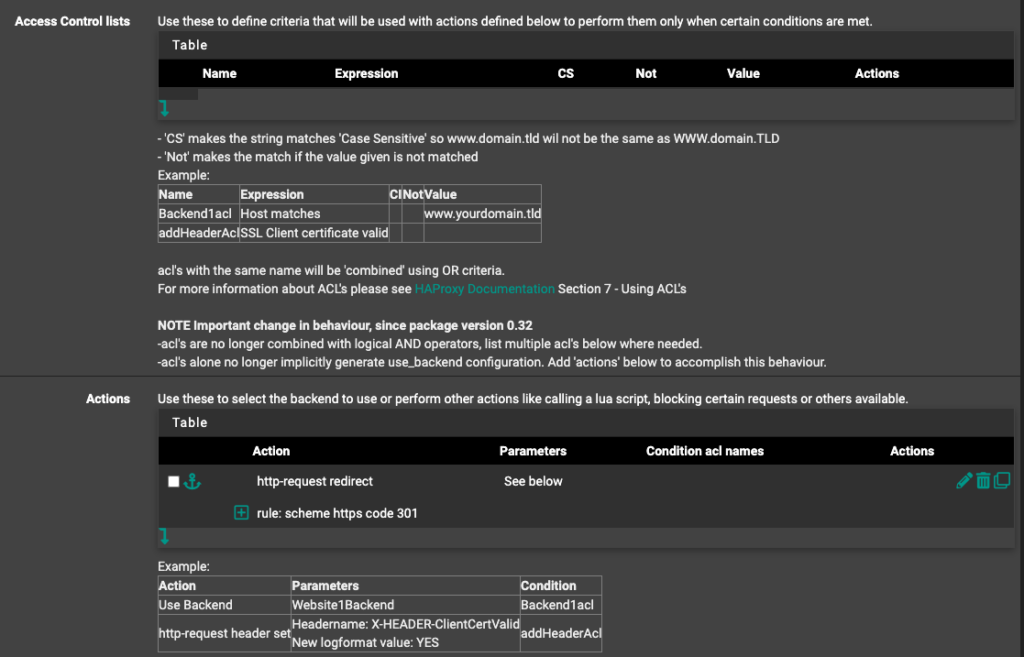
During my initial pfsense and HAProxy setup and configuration, I ran across the following blog saying to open port 80 to allow acme certificate renewals from Let’s Encrypt to occur without issue.
What Not To Do
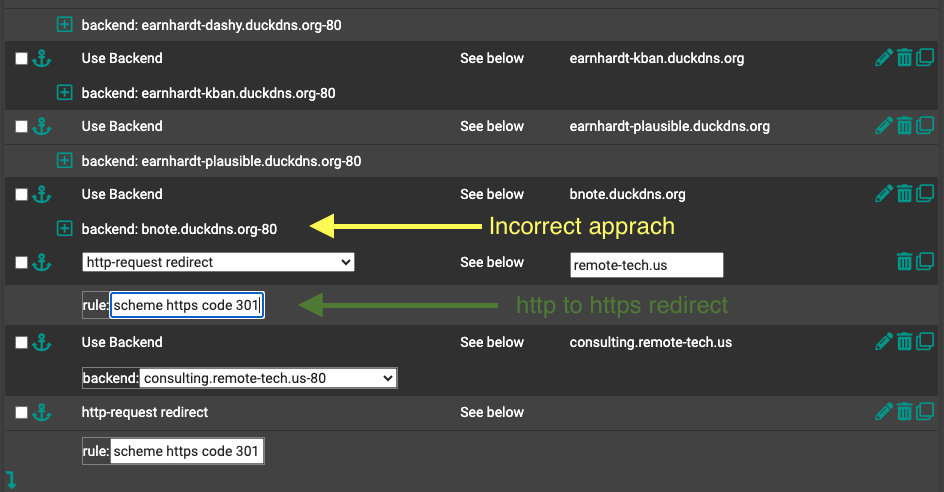
I incorrectly implemented a backend on port 80 that exposed my Unraid to the internet.
As shown in image below, I actually set up a backend connection on port 80 (http) for each endpoint just like I did with port 443 (https) frontend and because I never used http port 80, I didn’t realize what I had done until one day testing from outside my network, I accidentally entered http (instead of https) on browser address bar and was surprised that I was presented my Unraid login page.
–After some digging, I figured out what I had done incorrectly and corrected with a:
‘http-request redirect’ and a ‘rule:schema https code 301’
which now routes all incoming port 80 (http) traffic to port 443 (https).
Along the way I hit a few errors:
<sub><sup>config : parsing [/var/etc/haproxy_test/haproxy.cfg:169] : error detected in frontend 'shared-9480' while parsing 'http-request redirect' rule : expects 'code', 'prefix', 'location', 'scheme', 'set-cookie', 'clear-cookie', 'drop-query', 'ignore-empty' or 'append-slash' (was 'code:scheme').</sup></sub>
Until I came across this ha-proxy <a href="https://www.haproxy.com/blog/redirect-http-to-https-with-haproxy" target="_blank" rel="noopener sponsored" title="">article</a>.This new approach allowed me to remove 14 unnecessary backends and reduced my exposure.
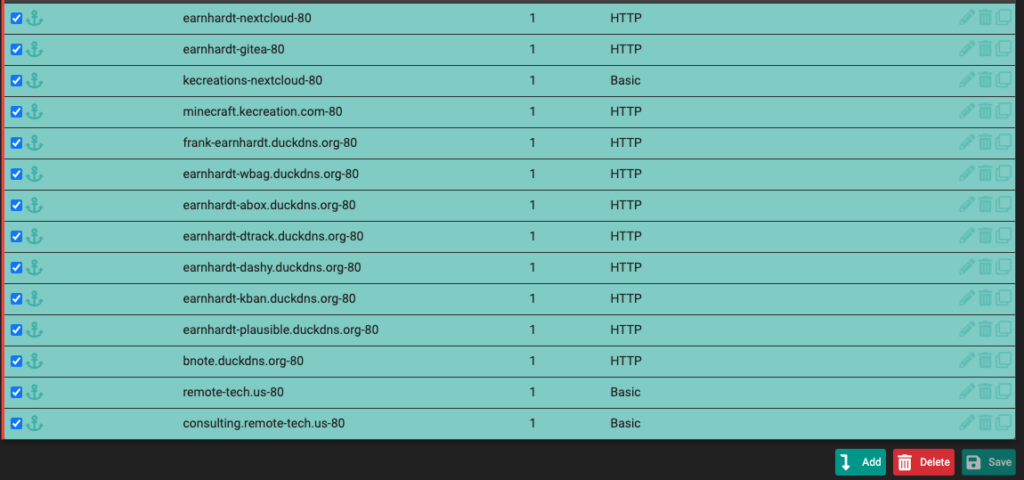
To continue this logic,
the frontend on port 80 (http) can be optimised to single ‘Action’ with a null ‘acl’ to catch everything thus allowing me to remove all ‘Access Control lists’